How many times have you opened a tab, only to navigate away from it for a few minutes, hours, or even overnight? When you return to that tab, having to log in again isn’t unexpected. After all, who keeps track of each page’s refresh schedule and log-out timer? Not us! This type of behavior makes web pages vulnerable to tabnapping, though — and this sort of cyberattack preys on users of sites that deal with private information, such as email providers and social media portals. Tabnapping relies on a user’s trust in the websites they’re familiar with, along with their inattention to detail, especially when it comes to the tabs they have open.
Note: Sometimes you’ll see “tabnapping” written as “tabnabbing.” The term “tabnapping” is a combination of “tab” and “kidnapping.” It stands to reason that “tabnabbing” is a combination of “tab” and “nab.” Either way, they both refer to the same scheme, and in our case, we’re going with the “tabnapping” version.
What is Tabnapping?
Tabnapping is a specific type of exploit and phishing attack. With tabnapping, the attacker creates websites that impersonate popular websites. Then, the hacker persuades users to submit their login information, including their passwords, to the phony site. Often, the fake websites look so much like the real websites users are used to seeing that they don’t notice the difference. The user thinks the website is genuine and doesn’t hesitate to enter their login information, as they always have.
What separates tabnapping from other types of phishing attacks (such as clicking a spoofed link in an email) is that the user doesn’t usually realize that the tab is phony. The fake login page loads in a tab that’s already been open in the browser for a long time. Most people wouldn’t think that a tab they opened themselves was taken over.
Tabnapping attacks are especially successful when the attacker can see the websites that the user loads often — they can then simulate the sites the user logs into regularly.
Let’s say you go onto your bank’s website with the intent of logging in. You head directly to the login page by typing in the URL yourself. But then you get caught up doing something else in another tab or window. After an hour or so, you click back into the bank tab because you’re ready to log in to check your accounts.
In the case of a tabnapping attack, by that point, the browser has navigated to a page that’s impersonating the bank’s page. But you will see a page that looks just like the bank’s page you’ve been on a hundred times and opened earlier that day.
How Tabnapping Works
In browsers, external links are able to open in new tabs or windows if the HTML HREF elements have specified target=_blank attributes. Unfortunately, this makes users vulnerable to tabnapping attacks. Sometimes, tabnapping is thought of as a design flaw in some browsers. However, while the browsers aren’t purposely vulnerable to hacking and manipulation, the design that allows for tabnapping is purposeful.
After a page loads and the tab has been open for a long time, browsers can navigate across a page’s origin in those inactive tabs. How? It has to do with the same-origin policy, an online security concept. This is when a browser lets scripts for one web page have access to data from another web page if both web pages have the same origin (hostname, port number, and URI scheme). The purpose of the policy is to prevent malicious activity. If there’s a malicious script on the first page, it’s prevented from getting sensitive data from other web pages. However, this security measure is also what makes tabnapping possible.
During an attack, the attacker sends a web page with the target=_blank attribute and embeds a malicious link in it. The user clicks the malicious link, which opens a new tab. Then, the hacker changes the first tab to a fake phishing page. This tricks the user into thinking they logged out of their account and have to log in again.
How Website Owners Can Prevent Tabnapping With the rel=”noopener” Attribute
Some browsers have extensions or other security measures that defend against tabnapping attacks. However, not all browsers allow the disabling of inactive tab redirects because there are cases where they’re legitimate. And since tabnapping isn’t very common (though still important enough for prevention measures), those browser vendors don’t want to risk breaking their applications for the sake of security enhancement. That means that some browsers may never have solutions or patches to prevent tabnapping. There are, however, still steps you can take to prevent this type of attack on your readers.
To prevent tabnapping on your website, add the rel=”noopener” attribute to any link that is set to open in a new tab or window. WordPress automatically adds this attribute for you when you add a link and then select Open in New Tab.
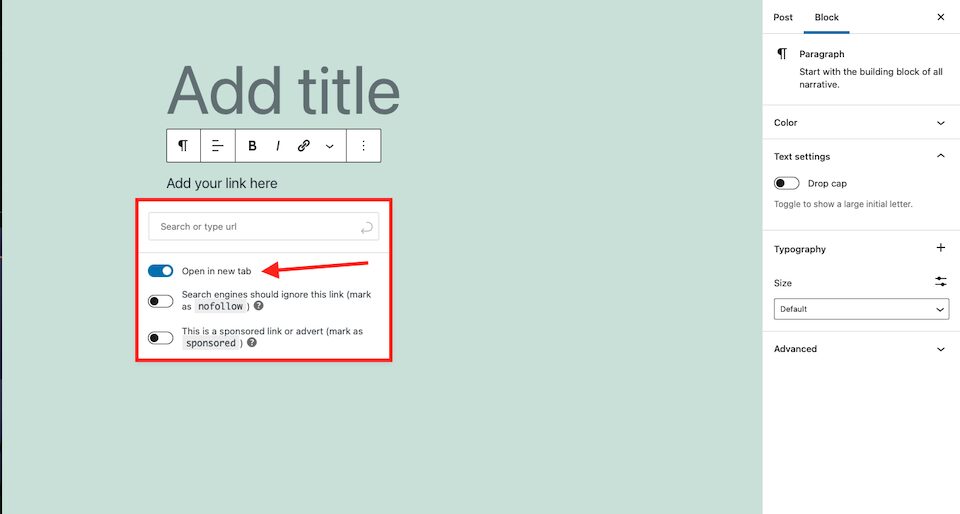
However, since rel=”noopener” doesn’t work on Firefox and some older browsers, there’s another attribute you should add: rel=”noreferrer” which WordPress also adds to links in new tabs if you’re up to date.
Whether or not you’re using WordPress, this is what your links should look like to prevent tabnapping:

How Users Can Keep Themselves Safe From Tabnapping
Major browsers usually have some kind of filter to weed out malicious sites, as well as legit sites with infections. As long as the blacklists of those sites are current, tabnapping attacks will likely be blocked. If you ever see a notice that a site you’re trying to go to has been compromised, heed that warning. It’s no joke.
Users should also always check the URL before they enter their login information, particularly if they have tabs that have been sitting open for a long time. It’s unlikely that the attackers will be able to fake the legit website’s URL, so that can be a dead giveaway that it’s a fake. Close the tab right away if the URL sends up a red flag. Do not type, click, or interact. Just close it.
Password managers are also helpful. If your login credentials are linked to the legitimate website, they should only populate when you’re on the actual website — not when you’re on a spoof site that looks similar. Password managers coordinate with the URL, not the business name. If you don’t see the login credentials pop-up, close the tab and start over.
Other Types of Browser Hijacking Threats
Tabnapping isn’t the only type of browser hijacking threat to be aware of. Cyberattackers have all sorts of ways to get your clicks and steal your info. In general, browser hijacking is software that changes how a browser behaves or appears, and it may also make changes to the settings. This all happens without your consent, of course.
As a result, the hacker can get revenue, collect your data and even log your keystrokes. Ultimately, they can steal your identity if they collect enough information to build a full profile of you. Types of browser hijacking include:
- Adware that floods your browser with pop-up ads that pay per click. This type of attack will usually slow down your computer because it uses up so many resources.
- Cookie tracking to keep tabs on what you do online. Bad actors can find out everything, from your location and IP address to which pages you view and what you search for.
- Redirection to dangerous web pages or search engines or replacement of your homepage or default search engine.
- Spyware that collects your private data, which is then traded in data markets (which also often ends in identity theft).
To defend yourself, stay aware of the state of your browser and watch out for the telltale signs of a hack, like the ones described above. Keep an eye on the browser’s add-ons, extensions, and plugins, too. If something goes awry after installing software, remove it immediately. You should also keep your browser clean with regular cleaning and cache clearing. And, of course, use antivirus software regularly, and avoid using public and/or unsecured Wi-Fi whenever possible.
Wrapping Up
To recap, tabnapping attacks make users think that they opened the tab themselves and that the site just timed out. The original page links to a second page, and the second page is able to rewrite the original page and replace it with a phishing site. Since the user started on the legitimate page, it’s unlikely they’ll notice that it’s a replacement. The page’s design looks like the original. When the user signs into the “original” page, their credentials are transmitted to somewhere else altogether.
To keep yourself as safe as possible from tabnapping, never log in on a tab that you didn’t open yourself. And even if you think you opened the tab, if you return to a login page after it’s been inactive for a while, close it to be safe, and then go back to the website to open a new one. Always check the URL, too. When it comes to other browser hijacking threats, practice good browser hygiene — limit and pay attention to the software you use, clear the browser cache regularly, and invest in quality antivirus software.
You may also want to read our article about cookie hijacking and how to prevent it.
Have you ever had your browser tabnapped? Tell us about it in the comments!
Featured image by Legend_art / Shutterstock.com
The post How to Secure Your Website Against Tabnapping and Browser Hijacking appeared first on Elegant Themes Blog.
